Meet our new CIO Berhanu Tadesse
Spring 2025
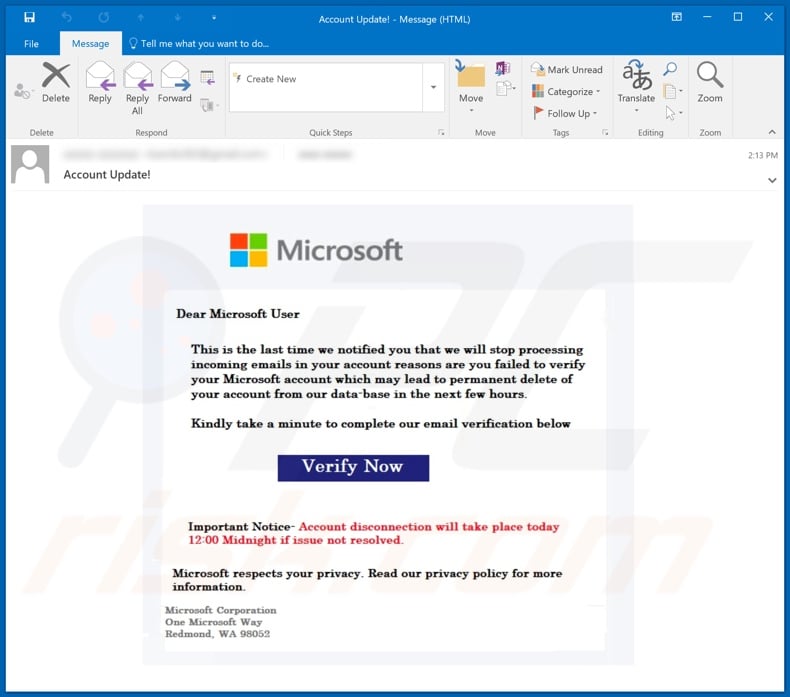
Phish | Verify Your Account
With the influx of new students, we have noticed a significant increase in phishing attempts. These emails often claim that your account needs to be verified or it will be deactivated if you do not act immediately.
What You Need to Know
- These emails are fraudulent
- Links may appear legitimate but redirect to a fake website
Remember
- We will never ask you to verify your account
- Do not click suspicious links or attachments
If you are unsure if the email is legit, you can always report it to the Help Desk and receive confirmation if the email is real or a phish.
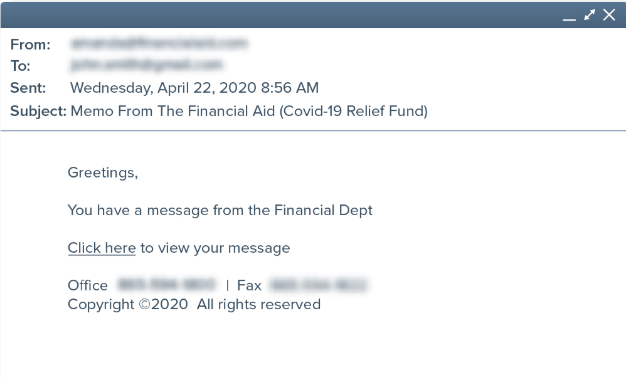
Phish | Financial Aid
With the Fall semester starting in a month, be wary of financial aid phishing if you are expecting communication from the Financial Aid Office. Be sure it is official communication from the CSULA Financial Aid Office before clicking any links and inputting your personal info or credentials on any site.
In the example below, if someone were to receive this email today, the subject line is already a clear indication of it being a phish. Before clicking links to any email, it is important to check who the email came from and whether it is from a legit source or a suspicious user. If you still aren't sure if the email is legit, you can always report it to the Help Desk and receive confirmation if the email is real or a phish.
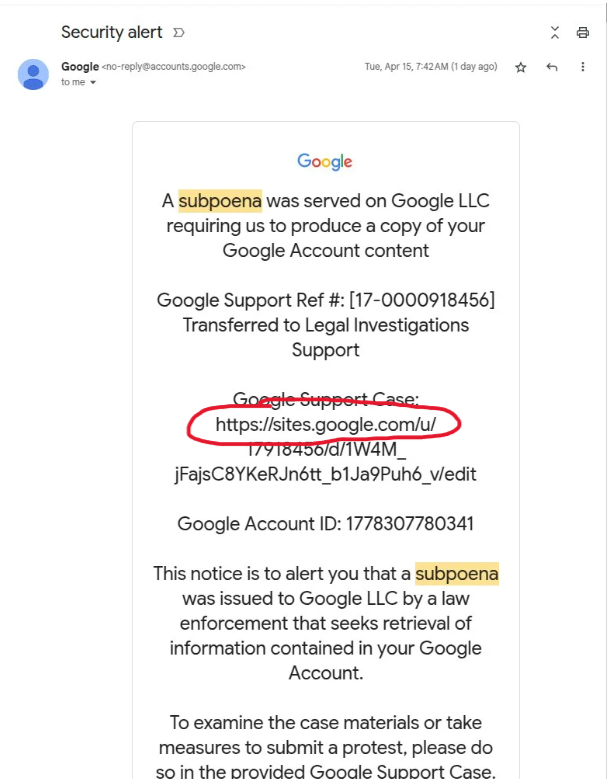
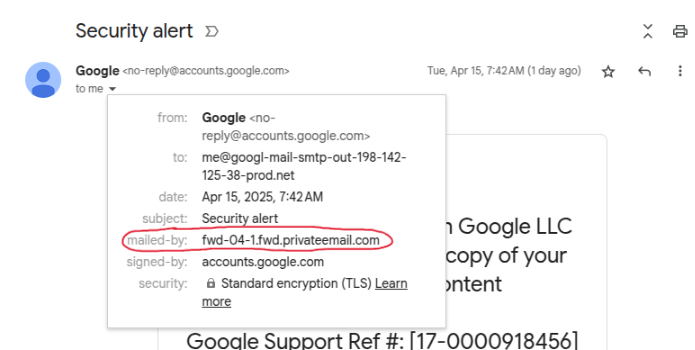
Google Spoof | Phish
In a recent phish, hackers were able to send a fake email that seemed to be delivered by Google themselves, bypassing security verifications and getting users sent to an identical looking support portal that collected login information. However, the support portal was being hosted on sites.google.com rather than accounts.google.com which is Google's actual support portal site. Hackers have gotten extremely good at disguising phishing emails to the point of mimicking Google themselves. Even though an email may be signed and delivered by a company you are familiar with, it's always important to check the email details to really see who actually mailed you the email. In this example, rather than mailed by Google, it was mailed by a privateemail.com.
Summer Job | Phish
As summer approaches, phishers will tempt you with promise of high paying summer jobs. Common signs of a summer job phishing scam can include the following:
Too Good to Be True - Working from home making $1,200/week with no experience.
Unprofessional Email Address - If an email is not from a company domain but rather from a free service like gmail.com or yahoo.com.
Weird Interviews - Interviews over a messaging app are suspicious since legit employers will do a video call or in-person interview.
Vague Job Description - Scam jobs will never explain the actual work you will do.
AI Spear Phishing
With the advancement of AI, cybercriminals now have an easier time with AI-supported spear phishing which has led to a click through rate of 54%. It has become increasingly easier for cybercriminals to generate phish emails with tailored messages and mimicking legitimate communication more effectively.
Before replying or clicking through an email. Here are some info and tips on what to look for in a suspicious email:
1. Unusual Sender Information - Subtle inconsistencies like mispellings or an unfamiliar email address.
2. Suspicious Links - Hovering over a link to verify its legitimacy.
3. Poor Grammar or Odd Phrasing
4. Inconsistent Branding or Logos - These could include watermarked logos or logos that look very similar to the original
5. Unexpected Attachments - Attachments that ask you to download files
6. Personal Information Requests - Legitimate organizations typically do not ask for sensitive information over email
7. Unfamiliar Greeting - Legitimate organizations with usually personalize emails with your name rather than something generic like "Dear Customer"
Social Engineering | Phish Scam
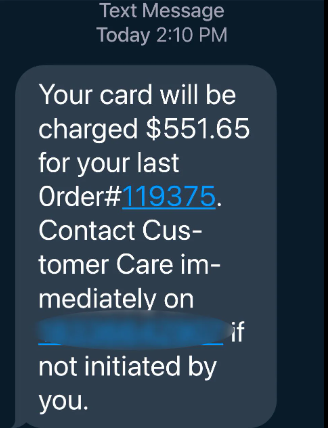
Social engineering phish scams account for almost 80-90% of all phishing attacks and are used to trick individuals into revealing their sensitive information, such as passwords, credit card numbers, or personal details. They will often appear as emails or text messages that seem legitimate. However, if you didn't request or expect the message, be cautious of clicking the links that were provided.
In the example, the phishers will scare you into thinking there were suspicious transactions on your account. However, when contacting customer service or a support team, they will never ask for your username and password or any sensitive information.
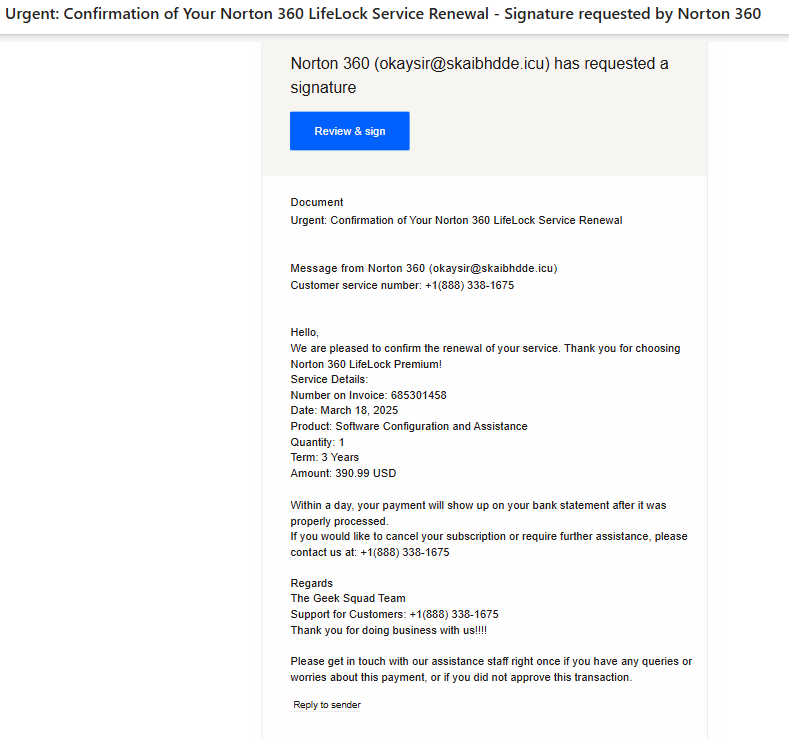
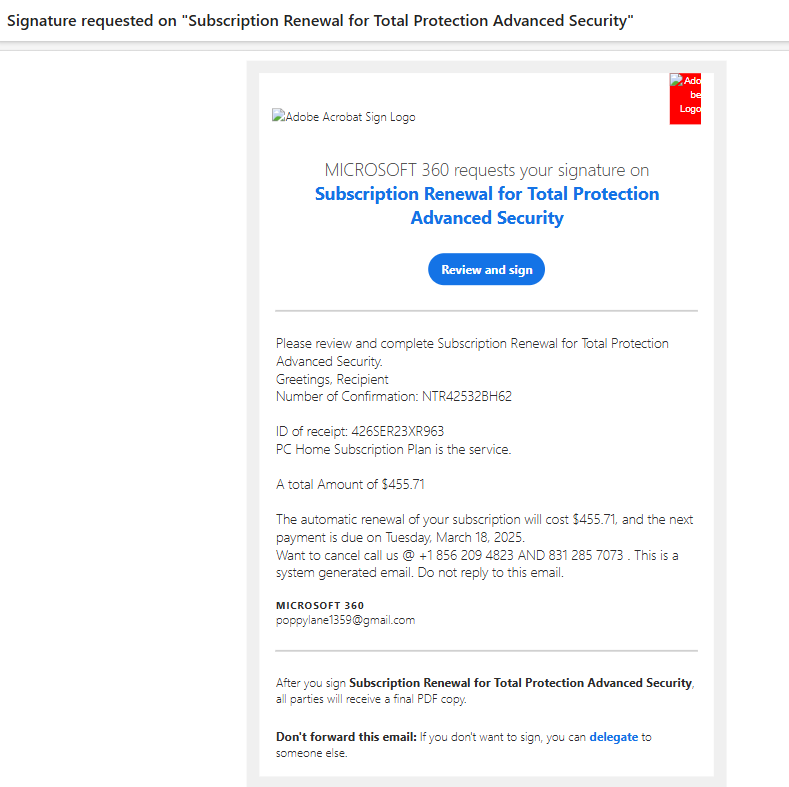
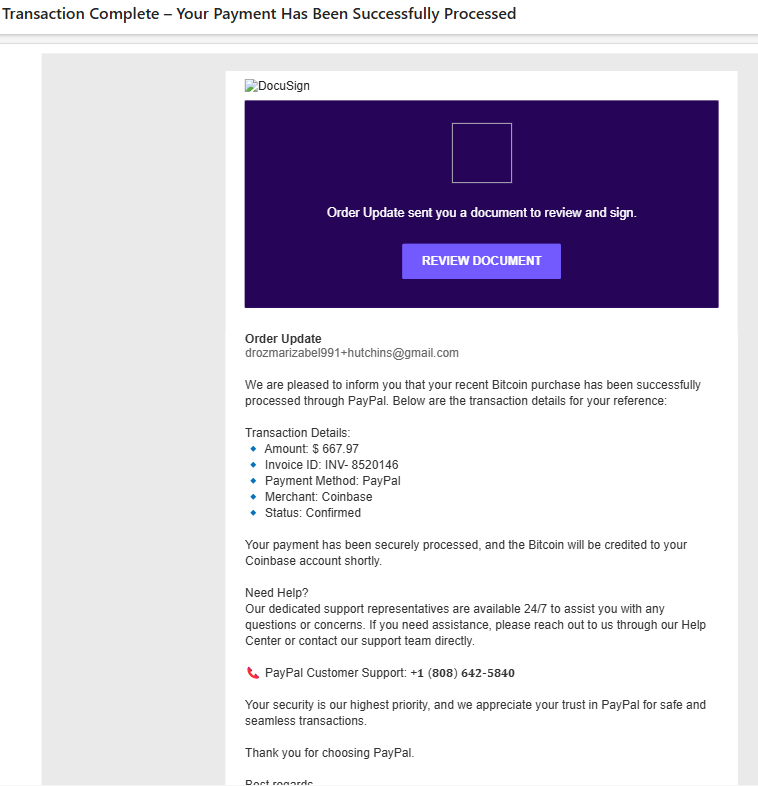
E-Document Signature | Phish Scam
Recently, there have been some electronic document scams going around asking you to review and sign a document for a subscription renewal or a successfully processed payment. These emails will usually have a clickable link or phone number to call for "customer support". If you did not make any payments, please ignore these phishing scams and avoid clicking any suspicious links.
Scam | Toll Road Fee
Recently there has been toll road scams going around through text, claiming that you have an unpaid toll balance and that payment is required to avoid late fees. Please ignore these fake texts and avoid clicking through suspicious links.

3 Quick Tips For Zoom Security
Adding a password or a waiting room for your zoom session.
To enhance the security of your Zoom session, you can add a password or enable a waiting room. This will ensure that only authorized individuals can access the meeting.
Only authenticated users are allowed to join.
By requiring authentication, you can restrict access to only those who have logged in through (calstatela.zoom.us), ensuring that participants are verified users.
Not allowing users that have (Guest) in their name.
Additionally, you can prevent users with "(Guest)" in their name from joining, as they are likely not part of the class and may not be authorized to attend the meeting.
For additional Zoom security tips, be sure to visit our website dedicated to keeping your Zoom meetings safe and secure.
Scam | Gift Card
A common scam circulating involves scammers requesting payment through gift cards. They often try to create a sense of urgency by threatening you with an immediate or pressing matter to rush your payment. If you ever receive such a request, the IT Help Desk can help confirm whether the email is legit or a scam.
QR Code Scam on Campus
Recently there have been QR codes placed on campus to pay for parking permits or daily parking. Please note that these QR codes are scams and are not approved by the campus. The only way to purchase your parking permit is through official channels like the Purchase Parking Website or the PayByPhone app for daily parking. You can find this site by accessing it through your SharePoint under the admin and finance tab. Please contact the Parking and Transportation Services if you have any questions related to purchasing a parking permit.
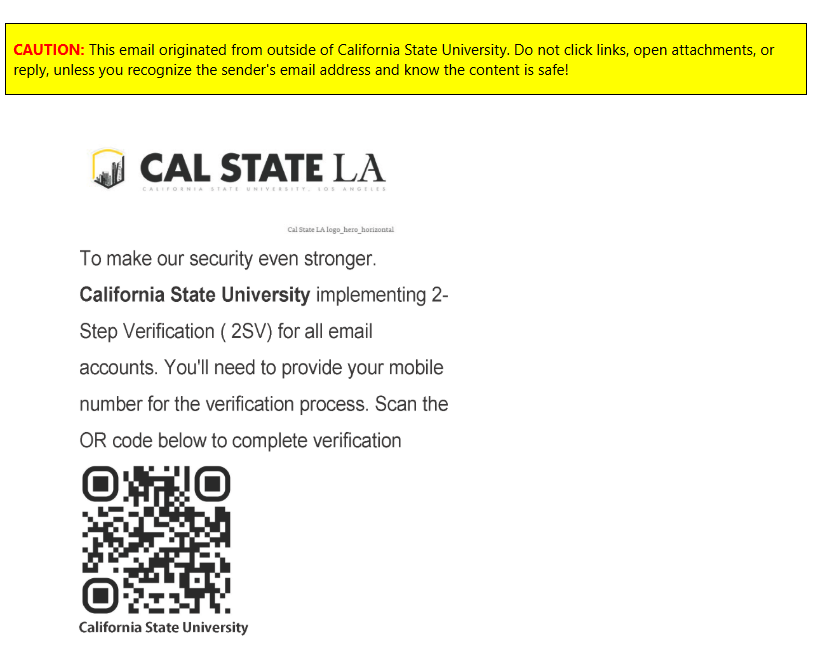
Scam | 2FV
In this phish, the phishers attempt to impersonate Cal State LA by using our logo but you can see a watermark in the bottom right corner which indicates they are not authorized to use the logo for "official business." Our campus also does not refer to 2-Step Verification as 2SV but rather MFA or 2 Step. We have also seen an increase use of QR codes from phishers so be careful when scanning QR codes and any directions that come from the website you are directed to.
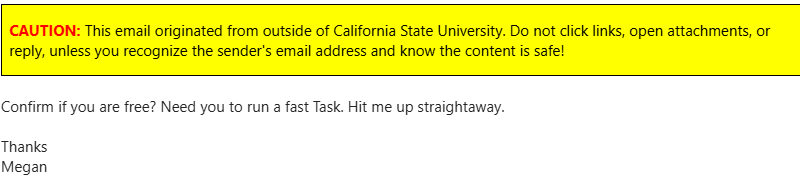
Scam | Fake Task
In this phish, the phishers are impersonating someone you may know or a school administrator. In this situation, reporting the message and not responding will be the best course of action.
Scam Impersonation | Duo Requests
If you receive a duo push that you did not request, you should decline it and report it after changing your password. A push that you did not request is an attacker that is trying to impersonate you and will use your account to scam others. Before accepting the push, be sure that you are the one that initiated the request to prevent any fraudulent activity.
Fall 2024
With the holiday season in full swing, scams are likely to increase. It's important to stay vigilant and be cautious when clicking links or entering personal information online.
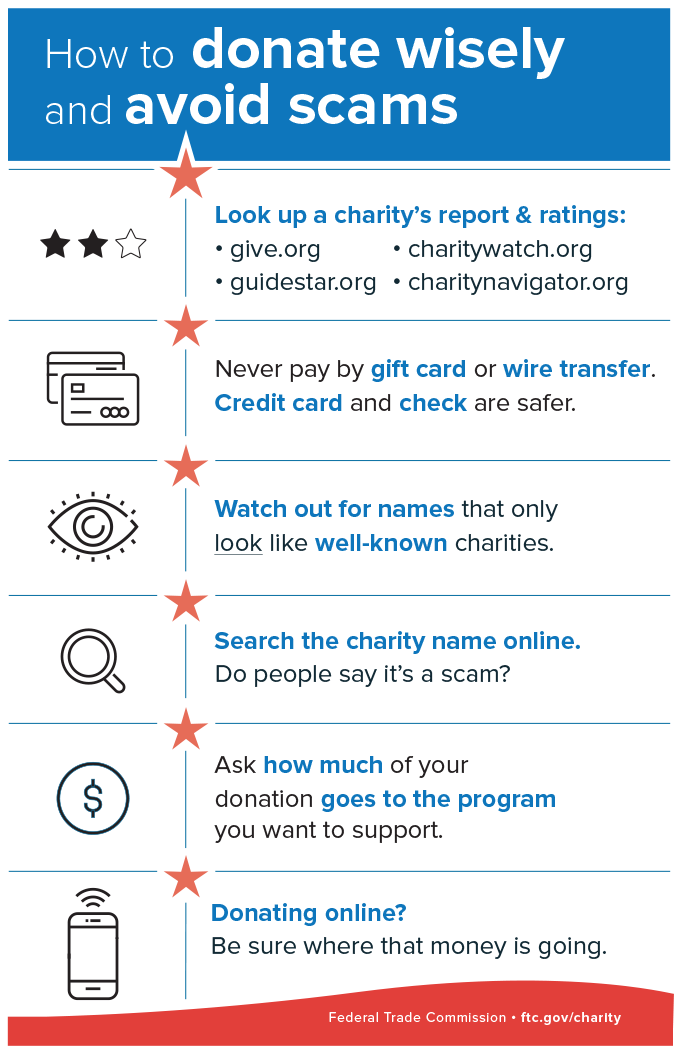
Scam | Fake Charity
During the season of giving, scammers will try to exploit people's kindness by creating a fake charity with a professional-looking website or use a similar name to well known charities. They will try to pressure you with emotional stories and urgent appeals to get quick donations. You should always be wary when donating and should verify that the charity is legit especially when you receive unsolicited calls and ask questions on what they will do with the money.
Scam Reminder | Social Engineering Attacks
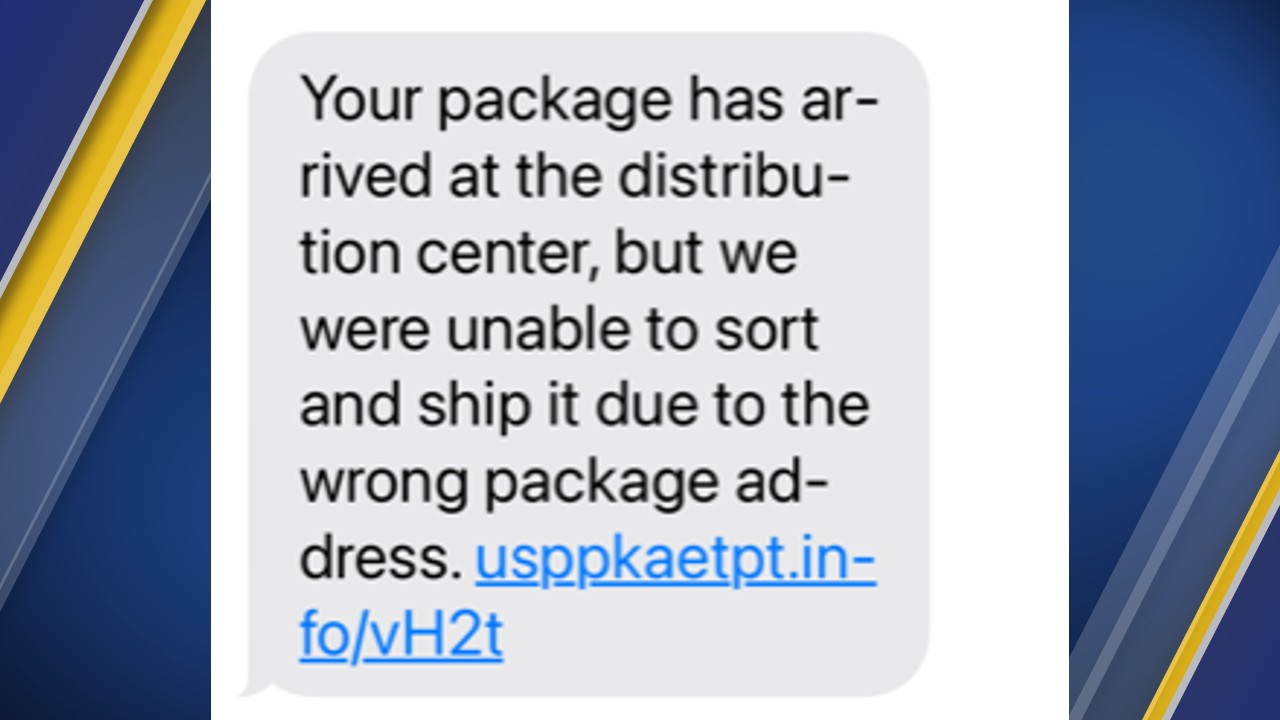
With Christmas fast approaching, attackers will start to increase the amount of SMS, phone calls, and emails being sent out. Messages can include items being unable to deliver due to incorrect/incomplete address or you were charged for an item you did not purchase. Never click on the links or "verify" your username and password using the links. If you ever have doubts, you should instead log into your official account and check it directly yourself.
Scam | AI Voice Cloning
Another scam to look out for are AI Voice Cloning Scams. Scammers will try to get a voice snippet of someone you know through their voicemail and will use AI to clone their voice. They will call and usually ask for money asap since they are in a pinch like stuck on the side of the road or need money to bail them out of jail. The best course of action is to speak to the person in question either in person, face time, or even just calling their personal number to see if they really are in trouble.
Scam | Pay In Advance
During this time of year, many different types of scams will happen when shopping online. One classic scam is the pay in advance scam for a special "limited" item. Scammers will pressure you to pay immediately and usually for an extremely low price. Best way to avoid this is to shop at well known retailers when shopping online.
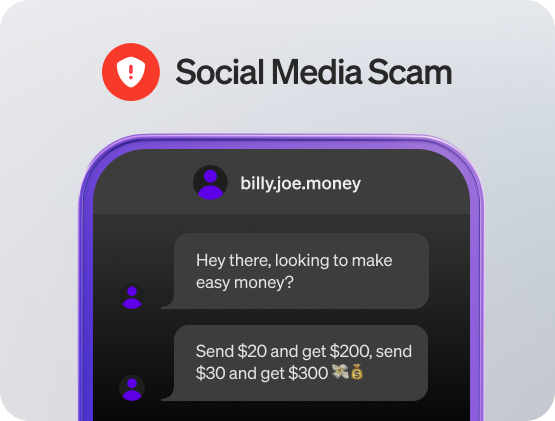
Scam | Cash Flip
Another scam that will start to increase would be a cash flip scam. Scammers will reach out to you offering to double or triple the money through their investment strategy. This happens especially during the holiday season when everyone is tight on money and it seems like a good solution for some extra money. However, this is just a scam and you won't be receiving any return on your "investment."
New Scam | QR Code
Recently there has been a QR code scam with in-store pick up from multiple retailers. Scammers will get ahold of your QR code and pick up your item without your knowledge causing you to lose your purchase. If you plan on buying online, it is highly recommended to change your email password before spending online.
Scam | Online Retailer Text and Phone call Scam Messages
During the holiday season especially Cyber Monday, text message and phone call scams from any online retailers will begin to increase in number. If you did not make any purchases, please avoid clicking on suspicious text message links or taking phone calls coming from online retailers or delivery services. You should always check your official accounts after receiving these scams to see if there are any orders or charges to your account.
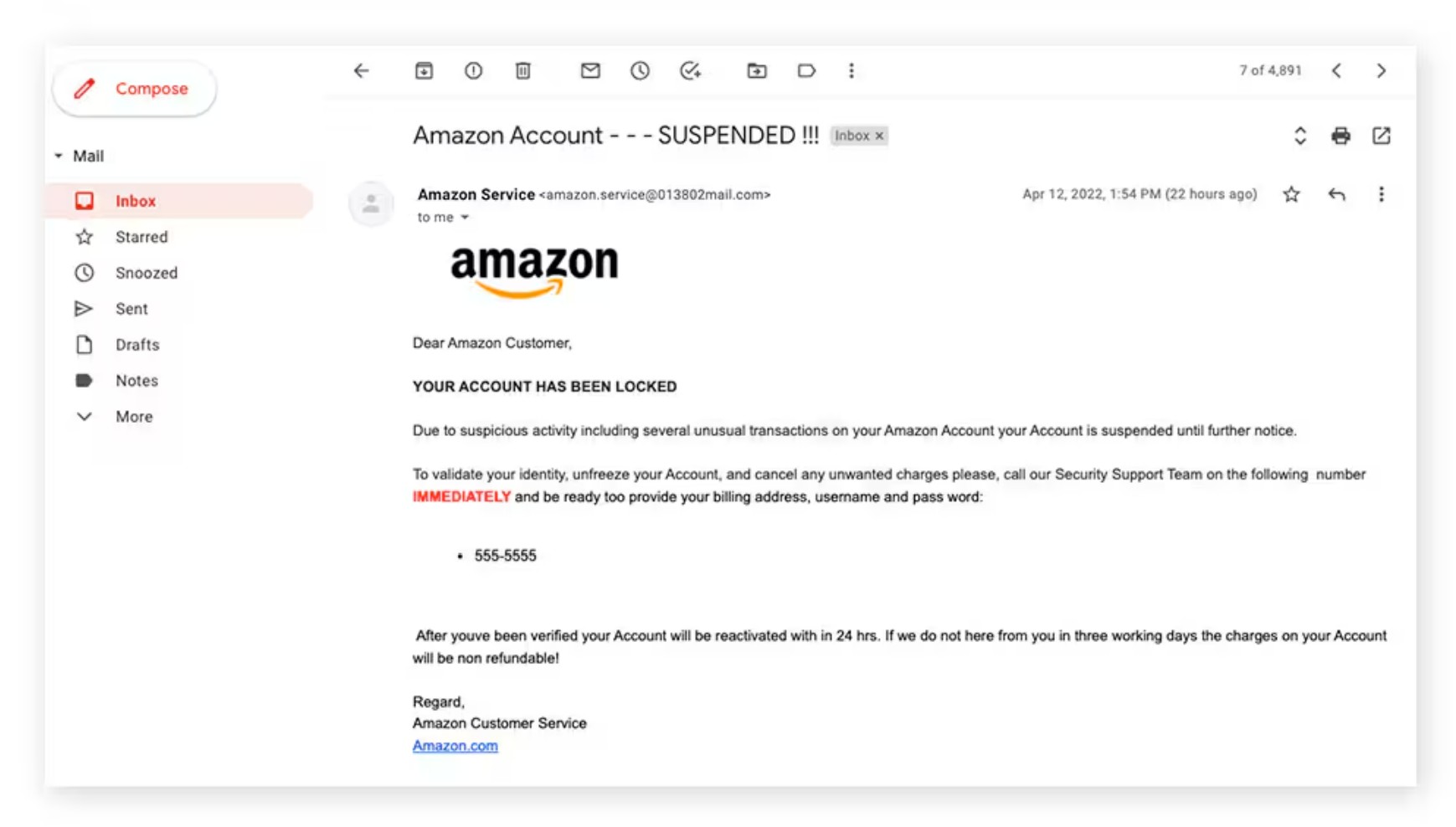
Scam | Amazon Text Message
During the holiday season, text message scams from Amazon will begin to increase in number. If you did not make any purchases, please avoid clicking on suspicious text message links coming from "Amazon." You should report the spam text to Amazon and check your official Amazon account to see if there are any orders or charges to your account.
Simple tips to stay safe online during the holidays:
1. Shopping online
Secure Wi-Fi - Shop securely - Pay wisely
When shopping online, it's important to be connected to secured Wi-Fi since public Wi-Fi can be vulnerable to hackers. In addition to secure Wi-Fi, be sure that the site you shop at has a https as the URL since that ensure the site is safe to submit payment information and/or personal details. You should try to avoid using your debit card linked to your bank account as your information can be stolen.
Resist the urge
With how expensive things are nowadays, scammers will push offers that sound too good to be true and that is usually the case. Be wary of emails and offers that provide a service or item for a ridiculously good price as it is most likely a scam. You should only shop from trusted online retailers.
Monitor your accounts
Especially during the holidays, it's important to check your financial accounts regularly for any suspicious spending. Nowadays with online banking, you can set up alerts for anything they find suspicious.
2. Giving Online
Research - Unsolicited requests - Payment
It's the holidays and the time of giving but it's important to know who you are giving to and if you are giving to the correct organization. You can first do research on who you want to give to and see how your donation can help them. Never feel pressured to give especially from unsolicited requests like emails or phone calls from organizations you aren't familiar with. If you do decide to donate, try to avoid wiring money or sending cash. Writing a check or paying via credit card is the safest and be sure their website URL contains a https.
3. Travelling
Free Wi-Fi - Confirm Network - Disable auto connect
Free Wi-Fi is great when travelling as it allows you to stay connected but it is important to know that most public Wi-Fi is not secure and can expose your personal information on your device. Auto connect on your device should also be disabled so you aren't connected without your knowledge and only manually connect to public networks that match the name of the establishment. Checking with staff is also a way to ensure the networks legitimacy.
Secure devices - Avoid shared computers
It's important to keep track of all your devices and to never leave them unattended as they can be compromised without your knowledge. It's also important to avoid using shared computers but if it is inevitable, never login to any personal sites using your credentials or make any purchase since the device may be compromised or the security software isn't up to date.
October events for Cybersecurity month.
| Cybersecurity Month | DAY(S) | DATE(S) |
|---|---|---|
| CSU Webinar Schedule for October | All October Long | |
| CSULA Stay Safe Online Webinar | 12PM | Wednesday | October 30 |
Various Announcements
We will be having our Cybersecurity webinar this Wednesday October 30th, at 12 pm. Come join us to learn about different ways to stay safe online. You can register for the webinar with the link above.
Phishing has been on the rise recently and with the holidays coming up, there will be bound to be more. If you are unsure if an email is a phish, be sure to report it to our ITS Help Desk and they can determine if it is a phish.
Cal State LA is also planning to move from My VPN to My Work vpn so be on the lookout for the switch.
October events for Cybersecurity month.
| Cybersecurity Month | DAY(S) | DATE(S) |
|---|---|---|
| CSU Webinar Schedule for October | All October Long | |
| CSULA Stay Safe Online Webinar | 12PM | Wednesday | October 30 |
Thanks to everyone who stopped by our tabling last week to learn more about Cybersecurity! We will be having a Cybersecurity webinar next Wednesday on October 30th at noon. Join us to learn about how to avoid the most common forms of cyber attacks.
October events for Cybersecurity month.
| Cybersecurity Month | DAY(S) | DATE(S) |
|---|---|---|
| Webinar Schedule for October | All October Long | |
| Tabling Session #1 9AM-4PM | Tuesday | October 15 |
| Tabling Session #2 9AM-4PM | Thursday | October 17 |
Come check out our tabling sessions this week on October 15 and 17. We'll have information on all things cybersecurity and you'll get a chance at some school bling.
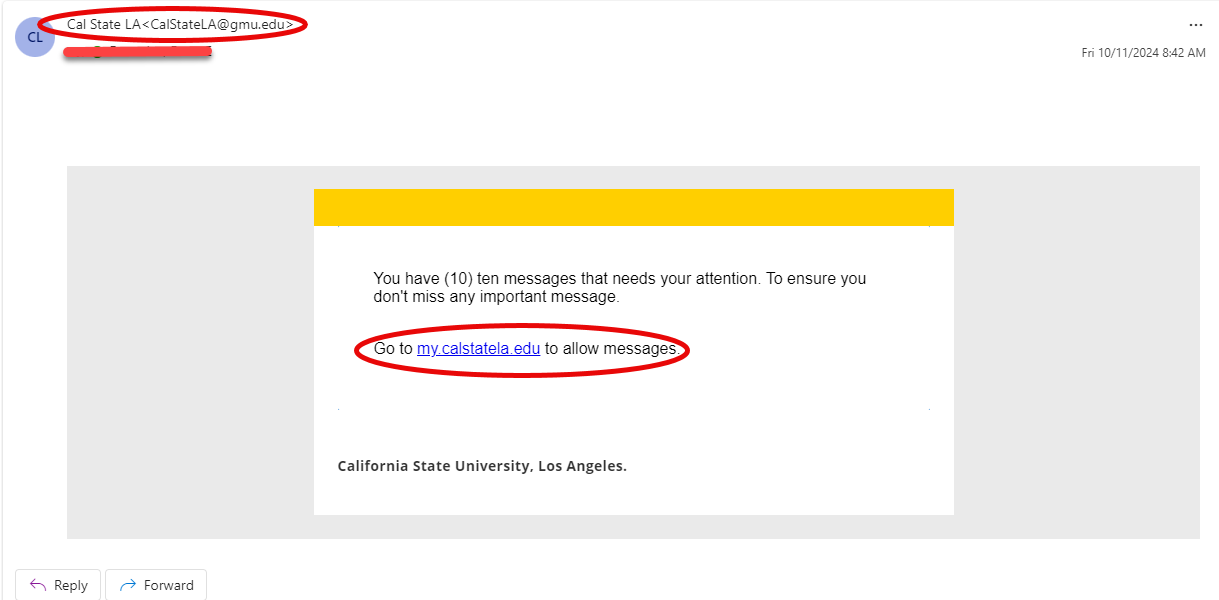
Phishing Example: Clicking Suspicious Link
This past week, there was a large phishing attack from someone impersonating Cal State LA. You should always check the sender's credentials and in the example, it comes from gmu.edu which is not CSULA. Be wary of suspicious links that may look familiar and always hover over links to check where the link will take you. We will also never ask for your credentials to verify your account.
October events for Cybersecurity month.
| Cybersecurity Month | DAY(S) | DATE(S) |
|---|---|---|
| Webinar Schedule for October | All October Long | |
| Tabling Session #1 9AM-4PM | Tuesday | October 15 |
| Tabling Session #2 9AM-4PM | Thursday | October 17 |
Come check out our tabling sessions on October 15 and 17. We'll have information on all things cybersecurity and you'll get a chance at some school bling.
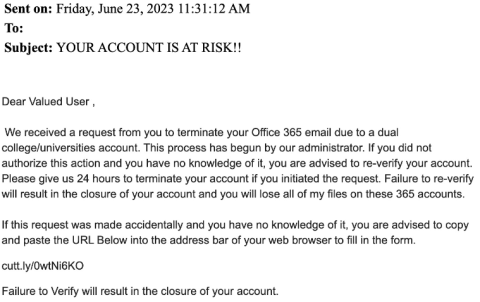
Phishing Example: False Account Deletion
Recently there has been an email claiming that your account is expiring and at risk of deletion. There is no need to worry since this is a phish which is aiming to get your credentials. Your account will never be at risk of deletion while being a student and official emails regarding your email will only come from the ITS Helpdesk.
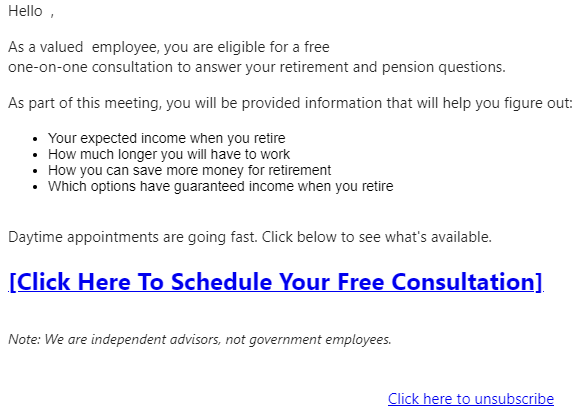
Phishing | Follow-Up: Retirement And Pension Meetings For Employees
We have been receiving numerous examples of the phish above from many different email addresses and domain names. We realize it is open enrollment period but please do not click onto these sites.
With Cybersecurity month coming, we would like to emphasize the importance of staying safe online.
4 simple steps to stay safe online:
1. Use strong passwords and a password manager
Your password should be at least 15 characters or longer and follow the specific requirements of the website. A strong password should be difficult to guess with a mixture of upper and lower case, numbers, and symbols. A password manager goes hand in hand with a strong password as it allows for more complex passwords, and in some cases, the password manager alerts you to a breach. Check out Cal State LA's strong password do's and don'ts requirements here!
2. Enable Multi-Factor Authentication
By enabling MFA, it adds an extra layer of protection even if your account password has been compromised.
3. Recognize and Report Phishing
It is important to recognize phishing so you don't fall victim to getting your information stolen, and reporting it will help you and your peers protect themselves from future phishing attacks.
4. Update all your Software
Software updates include patches for known security vulnerabilities, and hackers are unable to exploit the patched vulnerabilities. It also helps to reduce the chance of malware infections and security threats.
Check out this cybersecurity website for more in-depth information on how to keep yourself safe online.
October events for Cybersecurity month.
| Cybersecurity Month | DAY(S) | DATE(S) |
|---|---|---|
| Webinar Schedule for October | All October Long | |
| Tabling Session #1 9AM-4PM | Tuesday | October 15 |
| Tabling Session #2 9AM-4PM | Thursday | October 17 |
| Final Poster Judging (Cal Poly Pomona) | Thursday | October 17 |
With October around the corner, we will have a couple events which include 2 tabling sessions. There will be games and information on all things cybersecurity as well as a phishing quiz where you'll get a chance at some school swag.
| Cybersecurity Month | DAY(S) | DATE(S) |
|---|---|---|
| Cal Poly Pomona Poster Contest Due | Sunday | September 22 |
| Tabling Session #1 9AM-4PM | Tuesday | October 15 |
| Tabling Session #2 9AM-4PM | Thursday | October 17 |
| Final Poster Judging | Thursday | October 17 |
Phishing: Compromised Paypal Account Update
This phish example from last week has still been ongoing. The best course of action is to report it to the ITS Help Desk. Replying to these emails will not deter the phishers.
Phishing: Impersonation Emails
New phish attempts occurred over the weekend through Gmail. Phishers will impersonate a known faculty member to contact you. However, faculty will usually contact you through their Cal State email unless stated otherwise and be sure that the username matches with the name of the sender.
With Cybersecurity month starting in October, Cal Poly Pomona is hosting a poster contest on cybersecurity awareness. If you are interested, please check out their poster contest website for more details.
Phishing: Compromised Paypal account
In this phishing example, it will usually come from a compromised Paypal account. The phishers will try to have you think you've bought something and will ask you to call a number to verify in order to take your information. Deleting and reporting the email will be the best step, since replying will make it seem you are unaware of the scheme.
New Canvas Scam
There has been a scam on canvas which offers services to take classes in your place for money. If you receive this type of canvas message please report it to the ITS Helpdesk. This also goes against student conduct so please do not try to accept their offer.
Secure School Network
Be wary of public Wi-Fi and only connect to trusted networks. For a safe and fast connection on campus, use our campus secure network. Check out our website on how to log on with any device.
Phishing example: XXXX Shared a Document With You
In this example, the phishers pose as a known professor or administrator asking you to view their Google Docs by logging in with your username and password. Please note that you will never be asked for your username and password to view a Google Doc in an email.
Phishing example: CW Position with Direct Relief
In this example, the phishers will impersonate a reputable company and attempt to extract information through your resume. A quick Google search of these companies is easy and can provide information on whether or not the email you received is phishing. This phish is trying to impersonate DirectRelief, and by doing a quick search, their website tells us that they are aware of the phish and that it is a scam.
4 simple steps to stay safe online:
1. Use strong passwords and a password manager
Your password should be at least 15 characters or longer and follow the specific requirements of the website. A strong password should be difficult to guess with a mixture of upper and lower case, numbers, and symbols. A password manager goes hand in hand with a strong password as it allows for more complex passwords, and in some cases, the password manager alerts you to a breach. Check out Cal State LA's strong password do's and don'ts requirements here!
2. Enable Multi-Factor Authentication
By enabling MFA, it adds an extra layer of protection even if your account password has been compromised.
3. Recognize and Report Phishing
It is important to recognize phishing so you don't fall victim to getting your information stolen, and reporting it will help you and your peers protect themselves from future phishing attacks.
4. Update all your Software
Software updates include patches for known security vulnerabilities, and hackers are unable to exploit the patched vulnerabilities. It also helps to reduce the chance of malware infections and security threats.
Check out this cybersecurity website for more in-depth information on how to keep yourself safe online.
Phishing example includes: Phishing email titled "Quick Assignment" from xxxx@gmail.com
Hello XXXX
Reconfirm your phone# and look out for my text. I need an assignment completed quickly.
Thanks,
William Covino
In this example, the hacker has you provide personal information in an attempt to confirm they have a potential target or to send phishing through SMS. They will try to sound legit by using the name of someone you are familiar with but official emails from Cal State LA will always leave the email signature rather than just a name of the sender and will also not request personal information.
Phishing email titled: "XXXX Shared a Document With You" from xxxx@stxavier.org
XXXX shared a document
XXXX added you as a viewer. Verify your email to securely view this Document. You will need to verify your email every 7 days.
Google LLC, 1600 Amphitheatre Parkway, Mountain View, CA 94043, USA
You have received this email because it was shared with you from Google Docs.
In this example, the hacker provides a suspicious link for verification to a google document every 7 days. However, google docs may only require you to login to your email but does not require verification through a separate process. The hacker may also be attempting to get you to provide information by repeatedly accessing the site every 7 days. You can also determine if the link is trustworthy by hovering over the URL and this example you can see the URL takes you to a google form rather than a google doc.
Recent phishing examples include: Phishing email titled “SUMMER JOB OPPORTUNITY” from xxxx@gmail.com
Dearest Applicant's,
You are invited to explore a part-time work and study opportunity available to all staff or students. This position offers a chance to earn up to $550 weekly.
The job is exciting, flexible, and designed not to interfere with your current job or studies.
In this example, the hacker has you copied the suspicious URL to the browser rather than provide a direct link attempting to bypass the email security checking.
Phishing email titled “ACADEMIC INTERNSHIP OPPORTUNITY” from Career & Internship Fair hrmcare_er@xxxxhumanity.com
Greetings, valued students
I'm thrilled to let you know about some fantastic news. We've got a paid internship up for grabs, and it is work-from-home (remotely). Whether you're seeking part-time or full-time employment, this internship offers valuable experience for students across all departments.
Weekly payment of $450.00 APPLY HERE! Learn more about these amazing benefits.
With best wishes, California State University, Los Angeles Office of Student Services and Job Placement
In this example, the sender’s email address does not match with the claimed sender organization. There is also no Cal State LA official email banner.